Suche nach Kursen mit BeEdu
600+ Kurse
Environmental Impact Assessment
Learn how to conduct an environmental impact assessment (EIA). How do you undertake forms of development without compromising environmental, social, and economic sustainability? This four-week course will equip you with the skills to be able to decide what forms of environmental impact assessments (EIA) are needed and when to call on experts. Exploring real-world applications, you’ll see what successful EIA implementation looks like and how you can apply this to different contexts. With this knowledge, you’ll be able to develop in your current or future role as an environmental professional. Explore different forms of impact assessment. You’ll discover a variety of impact assessments including environmental, social, cultural, and economic impacts. This exploration will ensure you can gauge the impacts of development, how likely they are to occur, and how significant they will be. Align the EIA process with people. With an understanding of different impacts that can occur, you’ll unpack the nature of these impacts and how to assess them. This knowledge will help you explore the relationship between people and EIA. You’ll be guided through an environmental impact assessment process and how you can align this with the people involved, such as through engaging the community. Learn from the experts at The University of Adelaide. Throughout the course, you’ll be guided by the specialists at The University of Adelaide to ensure you finish with the knowledge and practical skills to conduct a successful environmental impact assessment. The skills you’ll learn are crucial for anyone undertaking an environmental impact assessment, but also for those managing or overseeing the process. This course is designed for anyone with an interest in environmental impact assessments, without any prior knowledge needed. The primary aim of this course is to develop the knowledge of professionals to assist them in advancing their career paths.
Designing and Implementing Cellular IoT Solutions
The webinar begins by introducing Nordic semiconductor and CASA, discussing how they work together to provide embedded solutions for IoT deployments. The speaker then covers practical tips for designing and implementing cellular IoT solutions, including navigating complexities in cellular IoT networks, maximizing security and coverage, and building low-power solutions. The webinar also touches on key topics such as roaming and coverage, SIM lifecycle, and getting data to the cloud. Examples are given for how these concepts can be applied in asset tracking and package delivery.
Don't Ruck Us Too Hard - Owning All of Ruckus AP devices | Gal Zror | NULLCON Goa 2020
Gal Zror presents a talk on his findings regarding Ruckus AP devices. He begins by asking if anyone is familiar with these devices, and then explains how he came across them at USA 2019. He notes that Rockers provides conference Wi-Fi and that their access points are also present in the current conference venue. Gal then shares his discovery of vulnerabilities in these devices and the potential risks they pose to users. He highlights the importance of understanding these findings and taking necessary measures to protect users' security.

Designing a Horror Game Character Using Blender
The video starts with the creator introducing themselves and the topic of designing a 3D character model for a horror game. They explain their premise and show their concept art, which they will use to create the 3D model. The creator demonstrates how to use Blender's modeling tools to create a basic human body shape and then modify it to fit the concept art. They highlight the importance of getting the overall shape and proportions right before moving on to details such as eyes, face, and features. The video also covers tips for creating unique avatars and shares experiences from the creator's freelance work. Throughout the video, the creator provides insightful commentary on their design process and offers helpful advice for those looking to create their own 3D character models for horror games.
Forward Progress Guarantees in C++ - Olivier Giroux - CppNow 2023
In this talk, Olivier Giroux delves into the concept of Ford progress guarantees in C++. He begins by explaining why Ford progress guarantees are important, as they provide a way to reason about program behavior in a deterministic manner. Olivier then discusses how C++'s abstract machine and memory model impact the behavior of programs that use Ford progress guarantees, highlighting the differences between C++ and other programming languages. He also touches on the implications of C++'s unique features for other languages that may not have their own Ford progress guarantees. Throughout the talk, Olivier provides examples to illustrate how Ford progress guarantees work in practice and why they are essential for building reliable software. By the end of the talk, viewers will have a deeper understanding of Ford progress guarantees in C++ and how they can be used to create more robust and predictable programs.

Digital Sovereignty: We need devices we truly own more than ever
Paul Gardner-Steven's presentation on digital sovereignty explores the degradation of freedoms in today's world and the importance of taking back control. He discusses how the concept of digital sovereignty is becoming increasingly relevant, particularly in light of recent events. Paul highlights his involvement in the open source community and how it ties into the idea of digital sovereignty. The presentation covers topics such as the coming digital winter, the importance of reclaiming control, and the role of the open source community in achieving digital sovereignty.

Sherlock Homepage - A detective story about running large web services - Maarten Balliauw
In this session, Maarten Balliauw shares their story of debugging large web services, specifically the NuGet server. They discuss the challenges they faced, such as frequent downtime, slowdowns, and errors, and how they went about fixing those issues. The talk covers various topics, including troubleshooting, bug fixing, and performance optimization. Maarten also shares their experience in using a detective approach to identify and solve problems in the service.

Stable35 Spy Vs Spy How to Use Breakable Dependencies to Your Advantage Stacey Banks Anne Henmi
The video begins with a disclaimer, followed by the hosts introducing themselves. They explain that they will be discussing how to use breakable dependencies for your advantage. Stacey and Anne share their experiences in using breakable dependencies in their work, highlighting the importance of understanding and leveraging these dependencies effectively. They emphasize that breakable dependencies are not just limited to technology but can also be applied to various aspects of life. The hosts provide practical tips and strategies on how to use breakable dependencies to achieve success in different areas, such as risk assessments, policy-making, and decision-making. They also touch on the importance of fighting dirty and fighting like a girl. Throughout the video, Stacey and Anne maintain a lighthearted and humorous tone, making the content engaging and easy to understand.

The 3 Way14 Attacking Packing Captain Hook Beats Down on Peter Packer Vadim Kotov Nick Cano
Vadim Kotov and Nick Cano present a three-way approach to unpacking malware, which they developed as an open-source tool called the 'packer attacker.' They explain that they wanted to provide a solution for independent researchers and academics to analyze malware at scale. The talk begins with background information on the topic, including the definition of 'packers' and how malware executes on a machine. The presenters then dive into the specifics of how malware unpacks and transfers control to its payload, using examples from their own research. They also discuss the importance of understanding malware at scale and the limitations of commercial solutions. Throughout the talk, Kotov and Cano provide detailed explanations of the techniques and tools used in their research.
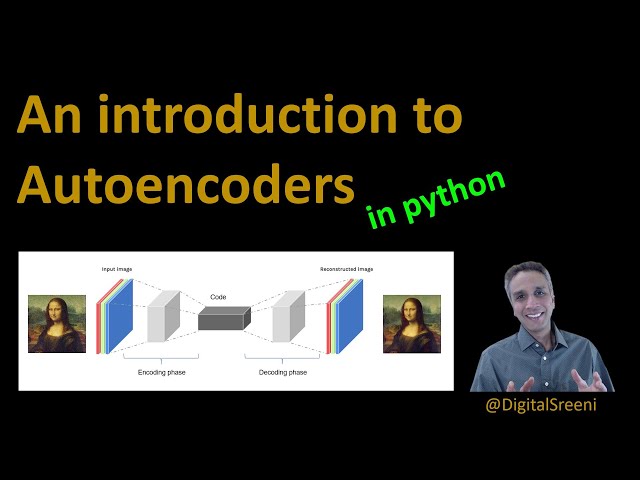
Understanding Auto Encoders: A Neural Networks Tutorial
Auto encoders are neural networks that are designed to reconstruct the original input image. In this tutorial, we will be discussing the basics of auto encoders and how they work. We will look at a few lines of code to understand how auto encoders are trained and how they can be used for noise reduction, colorization, and anomaly detection. Auto encoders are nothing but neural networks that are designed to reconstruct the original input image. When an input image goes through the auto encoding process, the dimensions are reduced down to a certain level, such as 8 by 8 or 4 by 4. The weights and biases are updated during this process, allowing the system to create a model that can tell how to take an input image and reconstruct the original image back. Auto encoders have various applications, including noise reduction in images, colorization of images, and anomaly detection. By understanding how auto encoders work, you can use them for these tasks and more. In the next upcoming videos, we will explore these applications in more detail.

Graphic Design
Class Central Tips Welcome to Graphic Design, the second course in the Effective Communications Specialization. Over 70 different companies have provided this specialization to their employees as a resource for internal professional development. Why? Because employers know that effective visual communication is the key to attracting an audience, building a relationship, and closing the sale. This practical course gives you the tools to create professional looking PowerPoints, reports, resumes, and presentations. Using a set of best practices refined through years of experience, you’ll: • make your work look fresh and inspired. • apply simple design “tricks” to begin any project with confidence and professionalism. • receive and respond to criticism and revise your project from good to great. "This course is fantastic. It teaches a great amount of starter graphic design information but it is broken down into easily understood videos and quizzes. The quality was top notch and the interaction was as good as you would get in a brick and mortar school. I did not feel like I was missing anything by taking it online." - a recent Graphic Design student All of the course assignments can be completed with basic presentation software such as Microsoft PowerPoint, Google Slides, or Apple Keynote. You’ll also have opportunities to explore and apply more sophisticated tools, such as Adobe Photoshop, Illustrator, and InDesign. This course can be taken for academic credit as part of CU Boulder’s Master of Science in Data Science (MS-DS) degree offered on the Coursera platform. The MS-DS is an interdisciplinary degree that brings together faculty from CU Boulder’s departments of Applied Mathematics, Computer Science, Information Science, and others. With performance-based admissions and no application process, the MS-DS is ideal for individuals with a broad range of undergraduate education and/or professional experience in computer science, information science, mathematics, and statistics. Learn more about the MS-DS program at https://www.coursera.org/degrees/master-of-science-data-science-boulder.

English Paper Piecing
English paper piecing is a method of quilting done entirely by hand, making it a great project for quilting on the go. Learn everything you need to get started from quilter Ashley Hough. Ashley will show you all of the materials you will need for English paper piecing, including fabric, a hand-sewing needle and thread, and both paper and plastic templates, which are used for cutting out the fabric. This class will cover some of the most common shapes used when doing English paper piecing, including the hexagon, clamshell, and diamond. Ashley will show you how to cut out your fabric using a template and ensure that it is larger than the paper template that the fabric will be sewn to. You will learn how to baste your fabric onto the paper using both a glue method and a hand-sewing method. Ashley will teach you how to baste different shapes, including those with straight edges, curves, and sharp points. Once you learn how to baste your fabric shapes, you will be ready to stitch your pieces together and remove the paper. You can then practice your English paper piecing with a fun, easy pattern download.

Efficient Enumeration Algorithms via Circuits
The video discusses a new approach to enumerating query answers using circuits. The speaker explains that traditional methods of query evaluation are inefficient, so they propose using intentional query evaluation instead. This involves compiling queries into tractable classes of circuits like DSDNNF, UBDDs, and others, and then evaluating the circuit to retrieve the answer. The talk covers preliminaries and states the problem formally, followed by a detailed explanation of how this approach can be used for tasks like counting, weighted counting, and probability computation. The speaker also discusses how these results can be applied to enumeration on circuits in general, and how they can be used to improve efficiency. Finally, the video concludes with a summary of the key points covered.
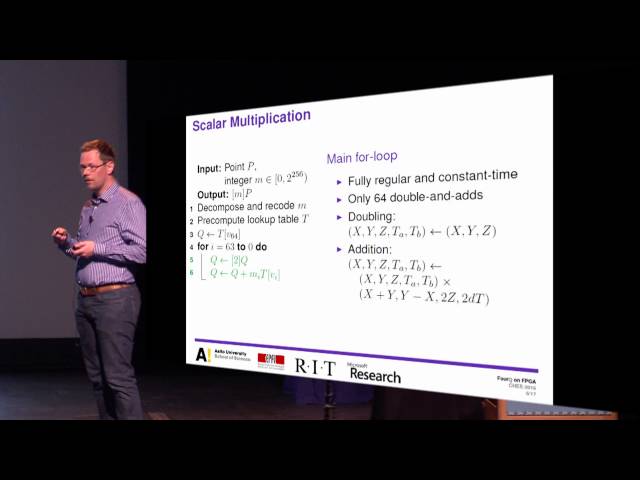
FourQ on FPGA New Hardware Speed Records for Elliptic Curve Cryptography over Large Prime Character
The video begins by introducing the new 4Q F-bit elliptic curve, a joint work of four researchers from different institutions. The speaker explains that this curve offers much higher performance than traditional curves, with evidence from benchmarks showing it to be two or three times faster. The presentation then turns to the question of how suitable this curve is for efficient hardware implementation, and the challenges that come with employing four downloads in a scale of decomposition. The speaker also mentions that 4Q was introduced by Craig Costello and Patrick Longer last year, making it a relatively new curve. The video concludes by highlighting the security offered by this curve, which is over 120 bits, thanks to its twisted Edward's curve with a cardinality of the group and a prime size of 392 times 246 bits. The speaker emphasizes that it's a very nice curve from many perspectives.

20 CSS Tricks You Probably Haven't Used Before
Have you ever heard about line-clap, conic-gradient or adjacent sibling combinator? In my classes, you’re going to learn some new & not very popular CSS tricks and properties that will help you to level up your web design skills. The classes are divided into small and tasty CSS chunks every followed by practical examples and exercise. The classes will cover properties such as: line-clamp, CSS counter (styling ordered list), custom bullet points, multiple backgrounds, vw & vh units, column-count, text-stroke, gradient text and much more! The course is destined for everyone who has ever written a line of CSS code. If you’d like to start from the basics, I strongly recommend you to explore my previous classes: Full list of the properties I'm mentioning in the course: Gradient Text First letter Numbered list Multiple backgrounds Filter blur Font shorthand Truncate text Line-clamp Cross-Browser Text Selection Color Character Units Custom Bullet Points Object-fit Conic-gradient Drop-shadow <wbr> Text-stroke Adjacent Sibling Combinator General Sibling Combinator Viewport height and witdh units Column count RESOURCES https://atom.io/ https://developer.mozilla.org/en-US/docs/Web/CSS/General_sibling_combinator https://developer.mozilla.org/en-US/docs/Web/CSS/Adjacent_sibling_combinator https://developer.mozilla.org/en-US/docs/Web/HTML/Element/wbr

Build a WordPress Travel Blog with Astra Theme 2023
In this tutorial, Alex will show you how to build a travel blog using the popular Astra theme and the free Spectra page builder plugin. He'll start by giving you a quick overview of what the video will cover, then dive into the process of creating a header that blends seamlessly with the background image. Next, he'll show you how to use different layouts for different pages, including a unique travel design layout. Throughout the tutorial, Alex will provide tips and tricks on how to optimize your blog for search engines and user experience. By the end of the video, you'll have a functional and visually appealing travel blog using Astra theme and Spectra plugin.
Anastasiia Tymoshchuk - Can we deploy yet?
The speaker begins by explaining that when working on projects in production, things can break easily. As a result, it's essential to make sure that your code is production-ready before deploying it. They share their experience as an organizer of Py Berlin meetups and how they've seen people struggle with this issue. The speaker then discusses the importance of testing and ensuring that code is reliable and scalable before deployment. They also emphasize the need to keep in mind the potential for things to break in production and to plan accordingly. The speaker concludes by inviting viewers to their next Pybrilimit app and encouraging them to share their experiences with the community.

Acrylic Painting: How To Paint A Realistic Seascape
Do you want to paint beautiful realistic seascapes in Acrylics? Then this class is for you. In this class, I'll show you my process of painting a realistic seascape and teaching you the techniques of creating layers and textures for creating waves and rocks on the beach. In this class, you will learn about: • How to build up different layers for painting a landscape/seascape • How to create the wave lines in a realistic way • How to create rocks on the beach and add light & shadow to give the 3D look • How to paint the beach and add textures of sand • My complete painting process from start to finishMaterials: 1. Acrylic Paints 2. Canvas Paper / canvas board / stretched canvas / wood 3. Brushes - 1 flat brush and 1 small round brush for detail work 4. A plate - something to mix paint on 5. Water 6. Tissue paper Colors I used in this class: 1. Titanium White 2. Prussian Blue 3. Dark green 4. Burnt Umber 5. Teal Blue (Light blue) 6. Purple 7. Black By the end of this class you should feel confident in your ability to create this painting and also any other seascape paintings. I recommend this class for everybody - no prior art experience is necessary. If u haven't painted in a long time and wanting to brush up your skills or if u haven't found anyone to mentor you in your creative journey, or if you are not sure you will be able to paint, or if you just want to paint pretty seascapes just to feel good - this class is for you. Look forward to seeing you in the classcheersDeb@debslilarts --------------------------------------------------- If you are new here, do check out my other classes and create masterpieces: How To Paint An Abstract Forest Landscape How To Paint Sunset Reflections How To Paint A Realistic Seascape How To Paint A Monsoon Landscape How To Paint A Landscape From A Photograph How to Paint Autumn Landscape with Knife How to Paint Sunrays Through Window --------------------------------------------------- You can purchase all the items I use by clicking on this link. This is an amazon affiliate link, meaning, at no extra cost to you, I will make a commission, if you click and make a purchase.

3D Architecture with Maya and 3Ds Max
Learn how to use Maya tools specific to understanding setting up the floor and then 3D’s Max for interior modeling What you'll learn: Learn numerous techniques on creating 3D models from the basic level to the most polished onesThe approach of the 3D Architecture Tutorial is entirely practical and it counts on real-time educationThe learners will be given practical knowledge about the process of ArchitectureThe 3D Architecture Tutorial highlights the all-important fundamentals of the software that a student can use without any confusion 3D Architecture or Architectural Visualization is the art of creating 2D and 3D images that contain the attributes of a proposed architectural design. Today, 3D rendering and architectural visualization software help the architects and designers to appraise proportions and scales using interactive 3D modeling and perform the effects of lighting, rendering and others.Using powerful 3D architectural and rendering software architects, designers and 3D artists can control designs in real-time, quickly transforming between concepts and reality by making and creating multiple versions of the designs. Maya, 3D Max, Rhino, VRay, Mental Ray, AutoCAD are some of the powerful 3D modeling and rendering software, that make amazing designs and attracts numerous clients today.3ds Max is a computer graphics program for creating 3D models, animations and digital images. It is one of the most popular programs in the industry today, having a great toolset for 3D artists. 3ds Max is an important part of many professional studios and is loaded with an efficient workflow and powerful modeling tools that is a time saver for most of the game artists.The real estate and architectural industries use 3ds Max to create photorealistic images of buildings in the design phase. The software creates seamless 3D geometry taken from the imported raw CAD files which are in the form of curves and paths.Maya is a 3D application software that is used to create animations and models with motion effects. Maya is used by creative professionals across the globe for producing visual effects for various Film and Television commercials to creating complex animations and effects. Maya software can also be used to create 3D models as well as interior design parts that can be used as digital prototypes. The modeling workflow built into Maya is designed to maximize the productivity of the users and enhance the design experience by having creativity and increased efficiency. Maya is also loaded with powerful tools that make complex animations easier to construct that is impossible to create manuallyThis 3D Architecture Tutorial aims to teach numerous techniques on creating 3D models from the basic level to the most polished ones. Learning high-end software 3DS Max is not an easy task, especially, when the user is a beginner. But keeping all this in mind, this course is designed to learn and master the software applications in easy and interesting steps. The approach of the 3D Architecture Tutorial is entirely practical and it counts on real-time education that will help us to know and master the industry standards.The learners will be given practical knowledge about the process of Architecture, and by the end of the course, the learners are made ready to create their artwork. The 3D Architecture Tutorial highlights the all-important fundamentals of the software that a student can use without any confusion. These valuable methods will help the learner to enhance the technical skills and have a good basic knowledge of the same.This program focuses on various applications & features of 3d Architecture for developing interiors and exteriors with Max and Maya. It helps the student in mastering the basics of the same. By learning these techniques, the learner can improve their skills at a major level. From Beginners to intermediate students, anyone can take up this course who is interested in learning 3d Architectural concepts on the software 3d Max and Maya.Students will go through a step by step process to create various interiors with the help of the lectures and sessions in the 3D Architecture Tutorial. With this training, the students will be able to master skills on Maya, 3ds Max, Bedroom Interiors, Basic Modelling, Interfaces of 3ds Max, Interior Modelling, Lighting and Rendering with Mental Ray & Texturing

Hack3rcon 3 20 Building a pad that will survive the times Branden Miller
In this video, Brandon Miller shares his insights on how to prepare for the end times by building a safe haven that can withstand any disaster. He covers various aspects of prepping, including creating a secure location, obtaining essential resources, and developing strategies for survival. He also discusses the importance of having a plan in place and being prepared for any situation. Miller's experience in IT and information security informs his approach to prepping, and he provides practical advice on how to protect oneself and one's loved ones from potential dangers. The video covers topics such as malware, reverse engineering, and management and policy, providing a comprehensive guide for those looking to prepare for the unknown.
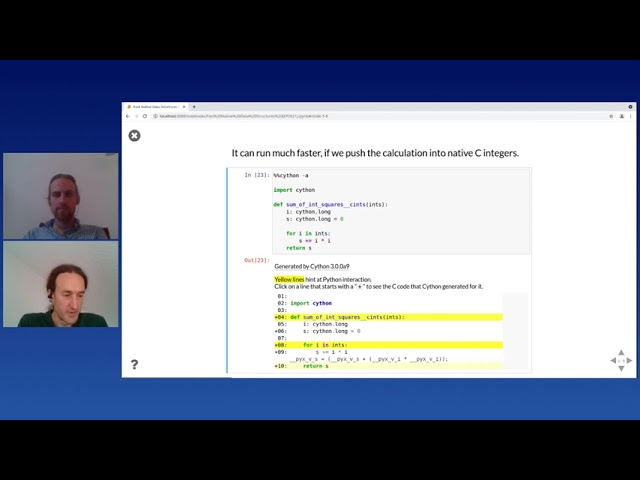
Stefan Behnel, David Woods - Fast native data structures: C/C++ from Python
In this talk, Stefan Behnel and David Woods explore the use of fast native data structures in C and C++ from a Python perspective. They begin by discussing the advantages of using native data structures, such as improved performance and reduced overhead. They then delve into the details of integrating these data structures into Python code, including tips for reducing memory usage and optimizing performance. The speakers also cover various use cases for fast native data structures, including scientific computing, machine learning, and database applications. Throughout the presentation, they provide practical examples and demonstrations to illustrate their points, making it an informative and engaging talk for both beginners and experienced programmers.

Business English: Networking
Class Central Tips This course begins with a welcome message and an overview of the Specialization. After this introduction, you will be asked to take a proficiency test to see if this course is right for you. During the course, you will begin learning vocabulary and customs related to socializing and networking in English. The goal is to enable you to interact with business contacts in person, on the phone and over email in a professional way. Course Learning Objectives • Determine whether the objectives of this Specialization align with your learning goals • Evaluate your current level of proficiency in business English communication • Present relevant information about yourself in a discussion forum • Develop your networking skills • Write short emails with appropriate formatting • Recognize and produce formal and informal language in emails • Develop vocabulary related to jobs and companies

Social Media Marketing Strategy: Objective Setting and Strategic Planning Essentials
Build a comprehensive social media marketing strategy. With this rise of mobile phones and connectivity, digital marketing through social media is now the single most important component of the marketing mix for many organisations. This is part 1 of a 4 part series. In Part 1, you’ll learn the step-by-step strategy setting tools and how you can get your message out and onto the screen. You’ll learn easy-to-use techniques to help you develop digital marketing plans that will make your product or service stand out from competitors. From organic to paid Throughout this course, you’ll learn how to harness the free elements of social media, craft perfect profiles and use the algorithms to your advantage. Getting organic traffic and interactions can be even more effective than paid marketing, you need a good strategy to get it right. You will try new paid marketing approaches, exploring strategies to hone your audience and get the most out of your spend. A practical approach Learn how to build a comprehensive social media marketing strategy, conduct an audit and set objectives. Throughout this course you will gain access to tools and templates that will empower you to put together a well thought out and evidence based social media strategy. People wanting to create a comprehensive social media marketing strategy, conduct an audit and set objectives

Phases of a Data Analytics Project
The video begins by introducing the course on data analytics using Excel. The speaker explains that the course will cover the phases of an analytics project, including data cleaning, data analysis, and data visualization. They then go over each phase in detail, highlighting the functions in Excel that are used in each one. During the data cleaning phase, the speaker discusses how to set up a problem statement, perform preliminary analysis, fix misspellings and character issues, remove duplicates, and check for bias. The video then moves on to the data analysis phase, where the speaker explains how to use functions like VLOOKUP, conditional formatting, data validation, and pivot tables to analyze data. Finally, the video covers data visualization using Excel, including how to create charts and graphs to present data in a clear and concise manner.
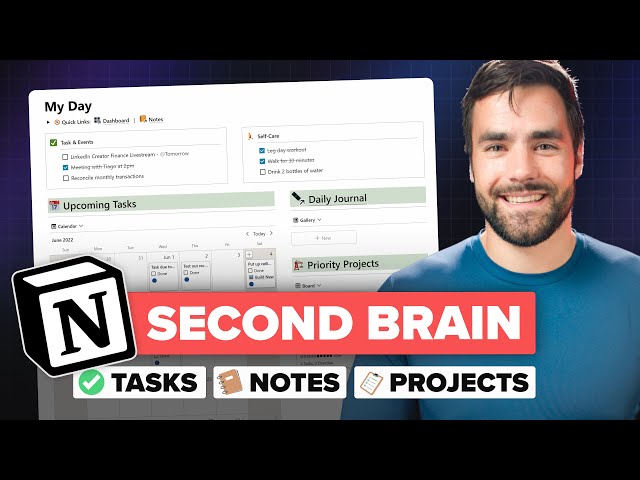
The ULTIMATE Second Brain Setup in Notion
Thomas Frank explains his complete second brain setup inside of Notion in this video. He shows how he uses the app to track all of his tasks, projects, notes, goals, and organizes his entire life using Tiago Forte's Para Organization system. The system is an all-in-one tool that Thomas has wanted inside of Notion since 2018 when he discovered it. He captures items quickly when on the go, organizes his life, and gets things done with the help of the GTD workflow inside the system. The video provides an in-depth look at every single part of this system from an action-oriented standpoint, including skipping around or reviewing as needed. Thomas also mentions that he has turned this entire system into a template that can be added to a Notion workspace for easy use.

Michael Spencer: Alignment in C++: Use, Limitations, and Extension
In this video, Michael Spencer provides an in-depth analysis of alignment in C++, including its definition, limitations, and potential extensions. He explains that everything in C++ is defined in terms of SD-Maxeline-T, and how alignment requirements are stored in every context. The speaker discusses the two different alignment forms: fundamental alignment and extended alignment, and highlights the importance of understanding alignment in C++ programming. He also covers the potential issues with alignment, such as over-alignment, and the proposals for addressing these limitations. Throughout the video, Michael Spencer provides valuable insights into the nuances of alignment in C++ and how it can be used effectively in programming.

Javascript for Pythonistas
The video starts by thanking the audience and introducing the topic of learning JavaScript for Python developers. The speaker then shares their experience working with both languages and explains how they use their knowledge of Python to speed up development in JavaScript. They highlight some of the key differences between the two languages, including the lack of type system in JavaScript and the use of callbacks instead of function arguments. The speaker also covers topics such as syntax, variables, loops, and functions in JavaScript. Throughout the video, the speaker provides examples and explanations to help viewers understand the concepts being covered. They also encourage viewers to ask questions and share their own experiences with both languages.

1 03 Dynamic Risk Taking and Social Engineering Chris Hadnagy
In this educational video, Chris Hadnagy explores the concept of dynamic risk taking and its significance in social engineering. He begins by defining risk and providing examples, before delving into five lessons he learned from being a risk taker. These lessons include understanding the impact of one's actions, embracing uncertainty, and recognizing the value of failure. Chris also shares stories that illustrate each point, offering valuable insights into the world of social engineering. The video emphasizes the importance of taking calculated risks to expand one's potential and achieve success, whether in personal or professional settings. Throughout the video, Chris maintains a jittery demeanor, revealing that he has been foiled by a prank from Dave, his colleague. Despite this, he remains determined to deliver an engaging and informative presentation. The video concludes with Chris encouraging viewers to take calculated risks in their daily lives, leading to personal growth and success.

Sentinel Lymph Node Biopsy (SLNB) for Breast Cancer
The video begins by explaining the purpose of the Sentinel lymph node biopsy for breast cancer diagnosis. It then delves into the technique involved in the procedure, including the identification of the sentinel lymph node and the removal of the lymph node for further examination. The clinical uses of the Sentinel lymph node biopsy are also discussed, including its ability to detect breast cancer at an early stage and improve patient outcomes. The video also highlights the potential complications that can arise during the procedure, such as lymphedema, and provides tips on how to minimize these risks. Finally, the video concludes by emphasizing the importance of accurate sampling and the potential benefits of the Sentinel lymph node biopsy for breast cancer diagnosis.

Creating Video Lessons with Online Video Maker InVideo
Learn how to create stunning video lectures using Article-to-Video templates from an online tool InVideo fast and easy! What you'll learn: Create a video by a text article for an online course or auto webinarLearn everything you need to know about InVideoCreate professional eye-catching videos that grab student’s attentionChoose and edit a video templateEdit video in a simple and intuitive online video makerWalkthrough examples from scratch In this course you will learn how to create a dynamic and attention-grabbing video lectures fast and easy with InVideo. Together we shall go through all steps of creating process, starting from InVideo features, designing a lecture by scenes, adding and editing a voiceover.You can use your article/post/thesis and get a custom video lecture in the end of this course. Or you can use the attached materials to this course: my company’s article on 4 Principles of Design in PowerPoint, a text for a voiceover and a script for each scene, graphic materials regarding the topic, and mp3 files for a voiceover.At InVideo online video maker you will work with:· more than 3000 unique hand-crafted templates with more than 100 templates being added every month;· in-built media library of more than a million images and stock footage (any topic and not only for a video course) to use from premium sources like Shutterstock and Storyblocks;· a background music of all genres by categories + automated voiceover that you can generate in any language!Together, we step-by-step will learn how to search and use and Article-to-Video templates and create a stunning video lectures for your YouTube channel, Udemy, SkillsShare courses, auto webinars for your business in Internet etc. You will do it fast and easy with intuitive InVideo editor.In the process of learning and as its result, you’ll get:· video editing skills;· a video lecture (mp4 file 2:32 minutes length) by NeitDesign article on4 Principles of Design in PowerPoint;· or your video lecture if you use your article.You can use InVideo editor absolutely free! All you need is to sign up at the website to log in to your cabinet and download the projects you’ll create.NOTE! With a free InVideo plan you’ll get:· full editing features, besides premium templates and premium media library resources;· access to all free in-build medial library resources of Pexels, Pixabay, Unsplash;· export up to 60 videos per month with a watermark.With any InVideo pricing plan you will get:· access to InVideo premium templates;· 1M+ Premium photos and videos from Storyblocks и Shutterstock;· export video lectures up to 15 minutes without watermarks and much more!More than 150000 people use InVideo across 150 countries. At the present, the editor interface is in English language, but you can type in your videos text in any language and use a multiple-language automated voiceover.InVideo opens new possibilities for online educators around the world. Use this opportunity to get to the new level of teaching your students!